参赛ID:1K0CT
shattered-memories
签到题 DIE查壳 无壳64x IDA64打开直接拼flag:
aplet321 | 接轨pwn
DIE查壳 无壳64x IDA64打开:
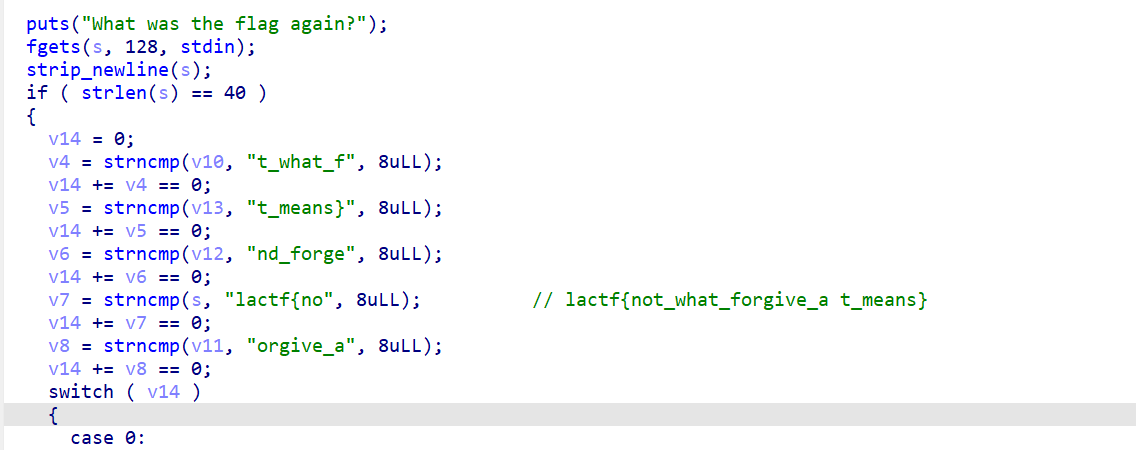
1 | int __cdecl main(int argc, const char **argv, const char **envp) |
逻辑是检测接收到的数据中包含连续的pretty或please的个数并要求含有flag 简单解解方程算出分别需要出现多少次 然后写出exp发送数据:
1 | from pwn import * |
the-secret-of-java-island | java逆向 | 爆破
一个按钮点击小游戏 目标是进入以下状态:
但是直接nc到该端口无法获得flag 还是要玩游戏 核心逻辑:
1 | if (paramInt == 0) { |
根据按钮点击情况向校验字符串添加d或者p然后求sha256哈希值进行校验 由于长度只有8可能性很少所以直接爆破:
1 | import hashlib |
然后在游戏中进行对应操作获得flag
flag-finder | GM逆向
文件包含data.win 说明是使用GameMaker编写的游戏 二进制文件只包含窗口消息的处理等最底层的逻辑 所以没必要太仔细分析 用目前最好的GM解包应用UndertaleModTool解包data.win

游戏的目标是找到key 但是地图上找不到 根据提示key一定在这个room中
在游戏Rooms中找到这样一个实例:
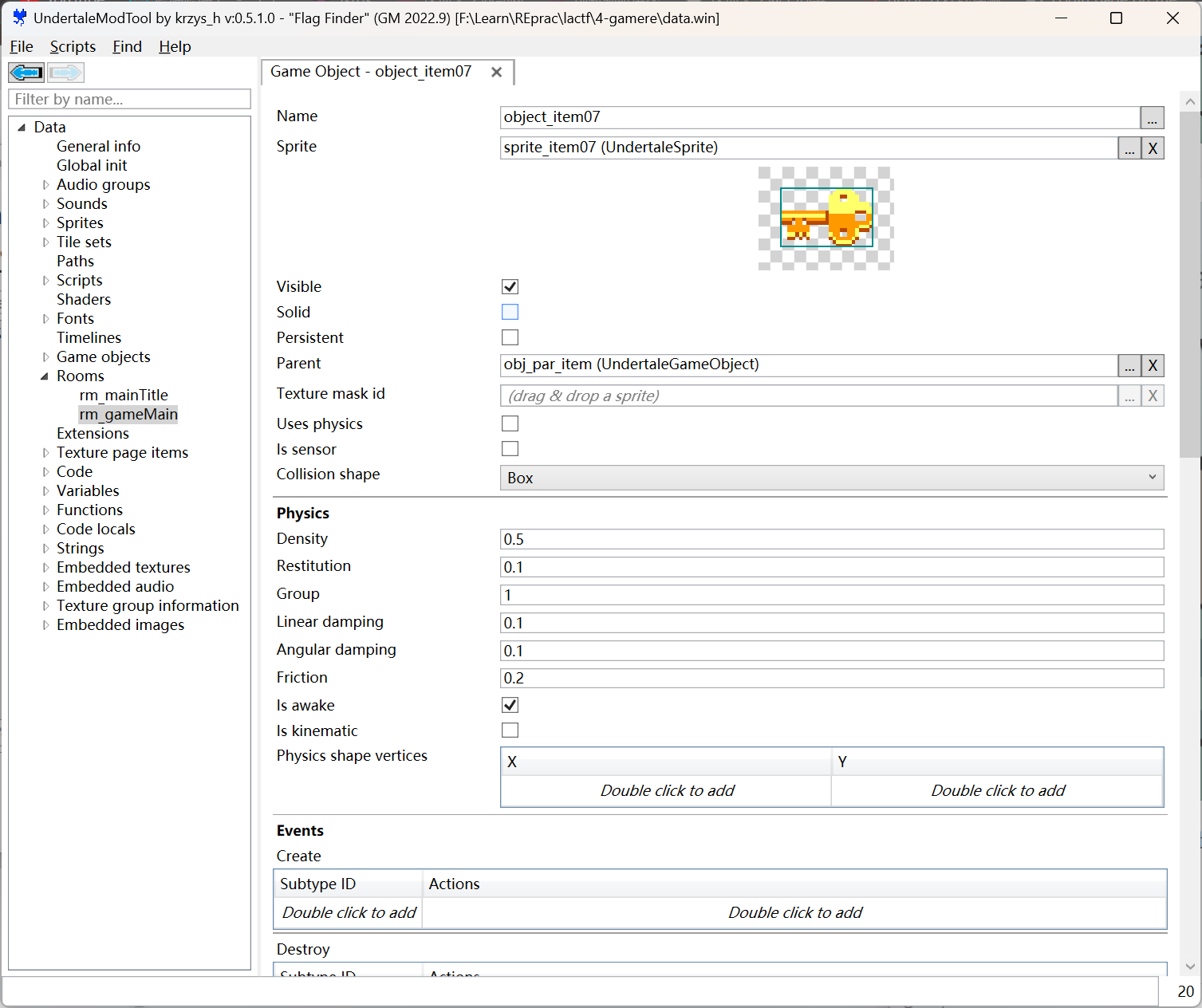
对应生成位置:
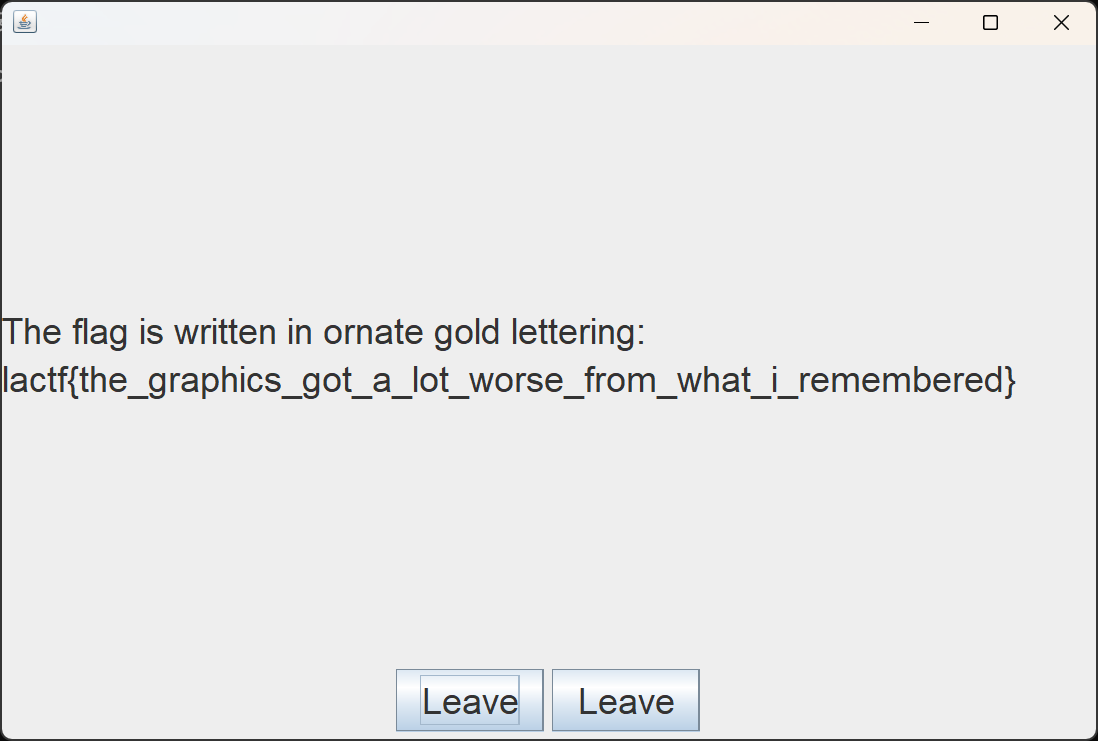
超出了地图空气墙范围 查看flag所在位置并将key修改到相近位置 UndertaleModTool支持直接运行修改后的data.win 完成任务得到flag:

glottem | algre
明文 直接notepad打开:
1 | #!/bin/sh |
数据e过长不展示 这个文件想表达的意思应该是输入的flag要分别满足python展示的代码和注释起来的java代码 java的逻辑很好理解 python代码的意思是保证flag内容中当前字符的位置作为1级索引来确定”层” 当前字符在表中的位置作为2级索引确定在层中的”段” 当前字符的后一个字符在表中的位置为3级索引从”段”中选取加数 题目提示flag长度34 去掉lactf{}后为26 而最后d就是要与260校验 python简单写个程序发现e中最小的数就是10 所以目标就是找到0~25层之间所有10的通路 结合java代码的逻辑最后写出脚本:
1 | e = [[[...], ...], ...] |
meow meow | 爆破
附件给了7个很大的data文件 先看二进制文件 DIE查壳 无壳64x IDA64打开:
1 | __int64 __fastcall main(int a1, char **a2, char **a3) |
输入的长度为5n 使用GOMP_parallel创建了func的线程 func:
1 | __int64 __fastcall sub_55811199B67A(__int64 input_proc) |
5 bytes一组用输入来控制文件指针 要求最后读到的数据中某处是0x63617400(cat\x0) 不知道怎么逆向计算出这5 bytes 直接爆破:
1 |
|
爆破花了5mins左右 不知道这是不是预期解 得到的flag片段刚好就是按顺序排列的 说明GOMP_parallel函数产生的线程的id就是从0开始递增而不是随机的
rbp | 函数控制
DIE查壳 无壳64x IDA64打开:
1 | __int64 __fastcall sub_71247(char *a1) |
通过栈帧可以得知sub_71850()实际上是mprotect() 直接点进去看不到
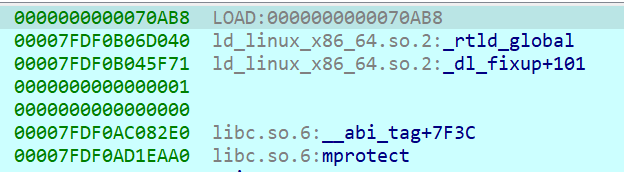
mprotect()可以设置程序对函数的权限(wrx) 7对应的就是wrx 3对应wr 所以被设置为7的函数可以执行 程序就是靠这个函数控制控制流的 据此可以分析出程序的所有逻辑:
1 | 1.读取到特定字母会导致count_2 += 1 |
动调中还发现读取到字母时就会触发两次main中的v4[0] = sub_710F9(不清楚原理 mprotect导致调试器无法正常触发断点 无法查看这个函数的汇编代码 估计是通过异常处理触发的) 据此写出脚本:
1 | key = [ord(i) for i in "vwbowpcjrhpkobfryuryuryu"] |
puzzlepalooza | Z3
DIE查壳 无壳64x IDA64打开:
1 | __int64 __fastcall main(int a1, char **a2, char **a3) |
z3求解符合条件的flag:
1 | from z3 import * |
technically-correct | ELF文件格式
总结
感觉大部分的题目考验的都是对代码的理解 并没有涉及非常神必的加密