终于审完wp可以放了(
父子进程通过ptrace进行通信, 子进程通过int 3向父进程发送信号, 父进程的处理如下:
1 | struct stream |
404850初始化了父进程的流水线操作, 父子进程之间没有数据通信, 所以加密过程完全由子线程实现, 所以重点关注父进程注入到子进程的call操作和jmp操作, 通过以下两个条件断点打印出子进程的指令流:
1 | # 402200 |
1 | # 40238D |
1 | # 402200 |
得到日志后让AI分析, 得出结论输入的第一步处理是AES-128, 密钥通过设置种子为0x10000后进行16次rand取最低字节生成, 两块16字节的数据加密完后通过第17次rand产生了最后加密使用的密钥:
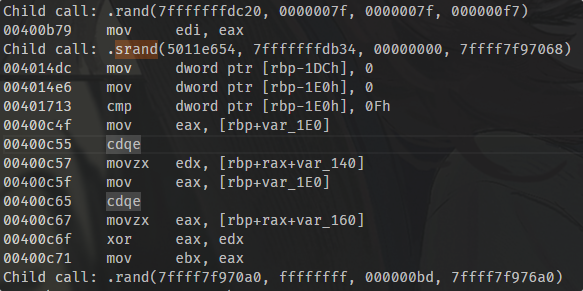
最后的加密是使用16字节固定密钥(在400A12处子进程进入时赋值)以及16次rand生成的16字节密钥进行异或, 后和4048F0中的字节进行对比, 两块16字节的数据分别与4048F0[:16]和4048F0[17:17+16]进行对比, 据此写出keygen:
1 |
|
1 | key = bytes.fromhex(key) |